3. Giving Access To Azure Key Vault
Prerequisites
Introduction
Enabling Azure Key Vault Certificate Automation requires EZCA to have access to your Key Vaults. EZCA needs RBAC Reader Role to verify the user requesting the certificate has access to the Key Vault. EZCA CA also requires an access policy with the following certificate permissions: Get, Update, and Create.
Adding Application to RBAC in Azure Portal
- Login to https://portal.azure.com
- Navigate to the Key Vault you want EZCA to manage.
- Click on the Access control (IAM) menu option
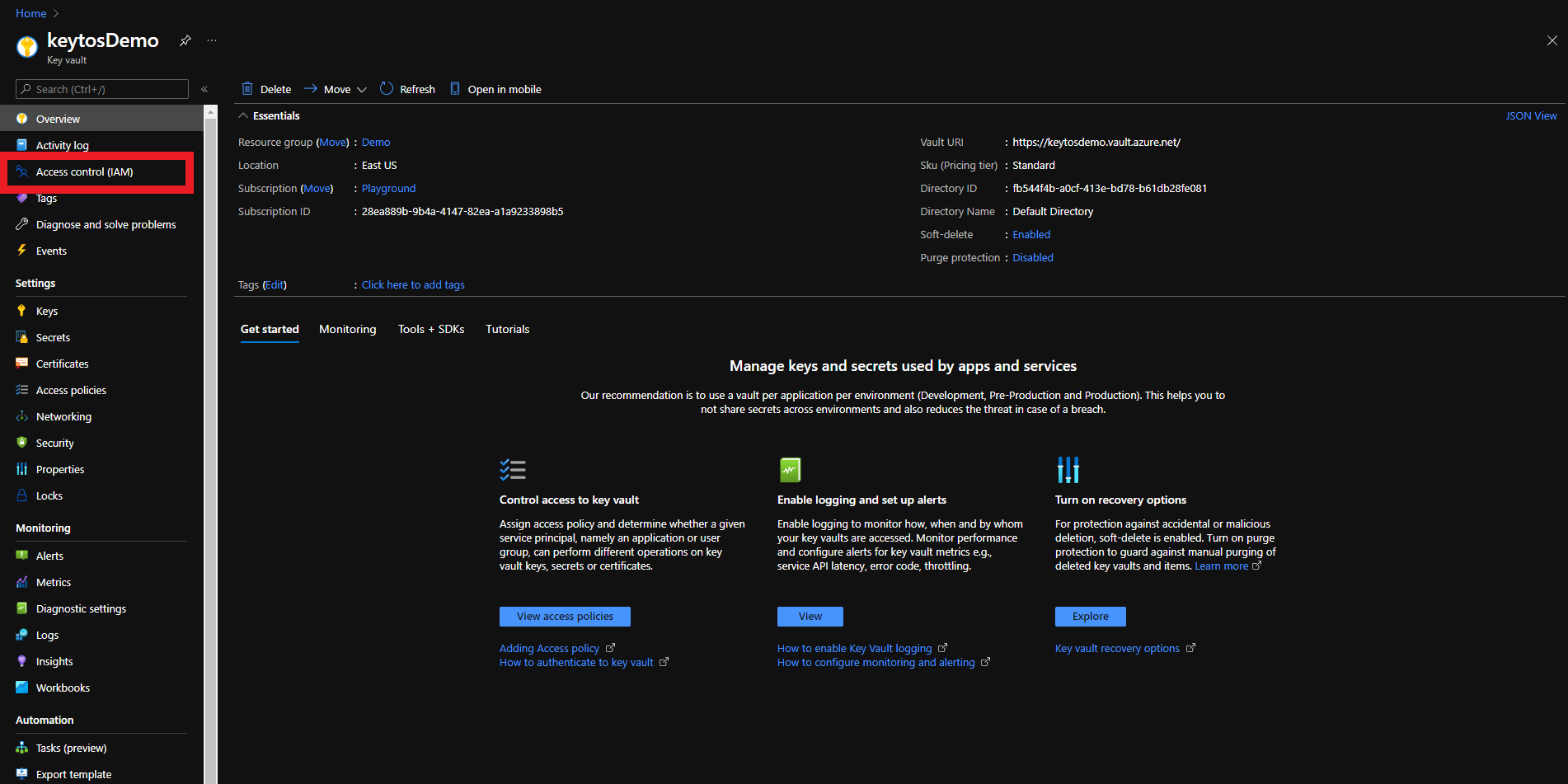
- Click on Add
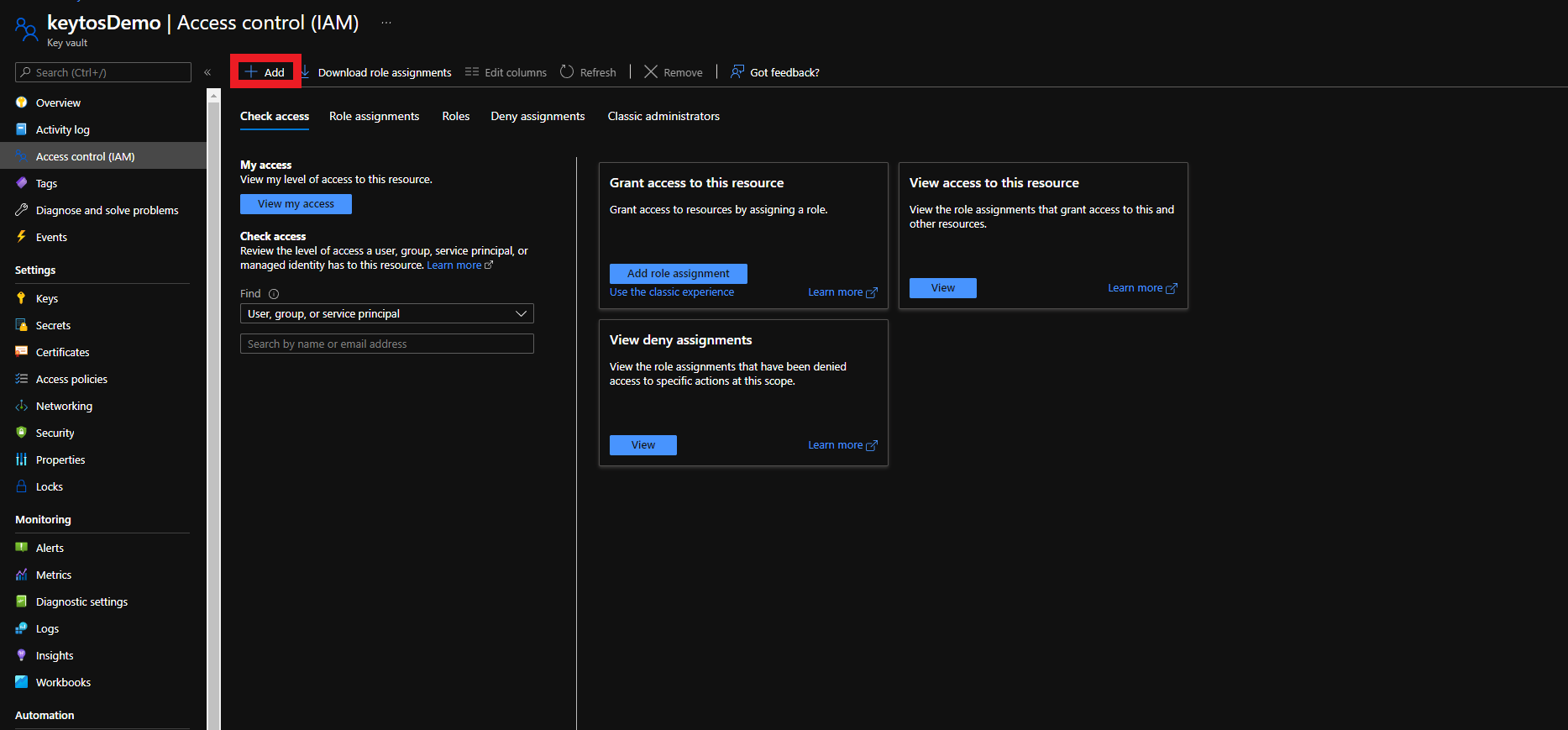
- Select the “Add Role Assignment” Option
- Select Reader role
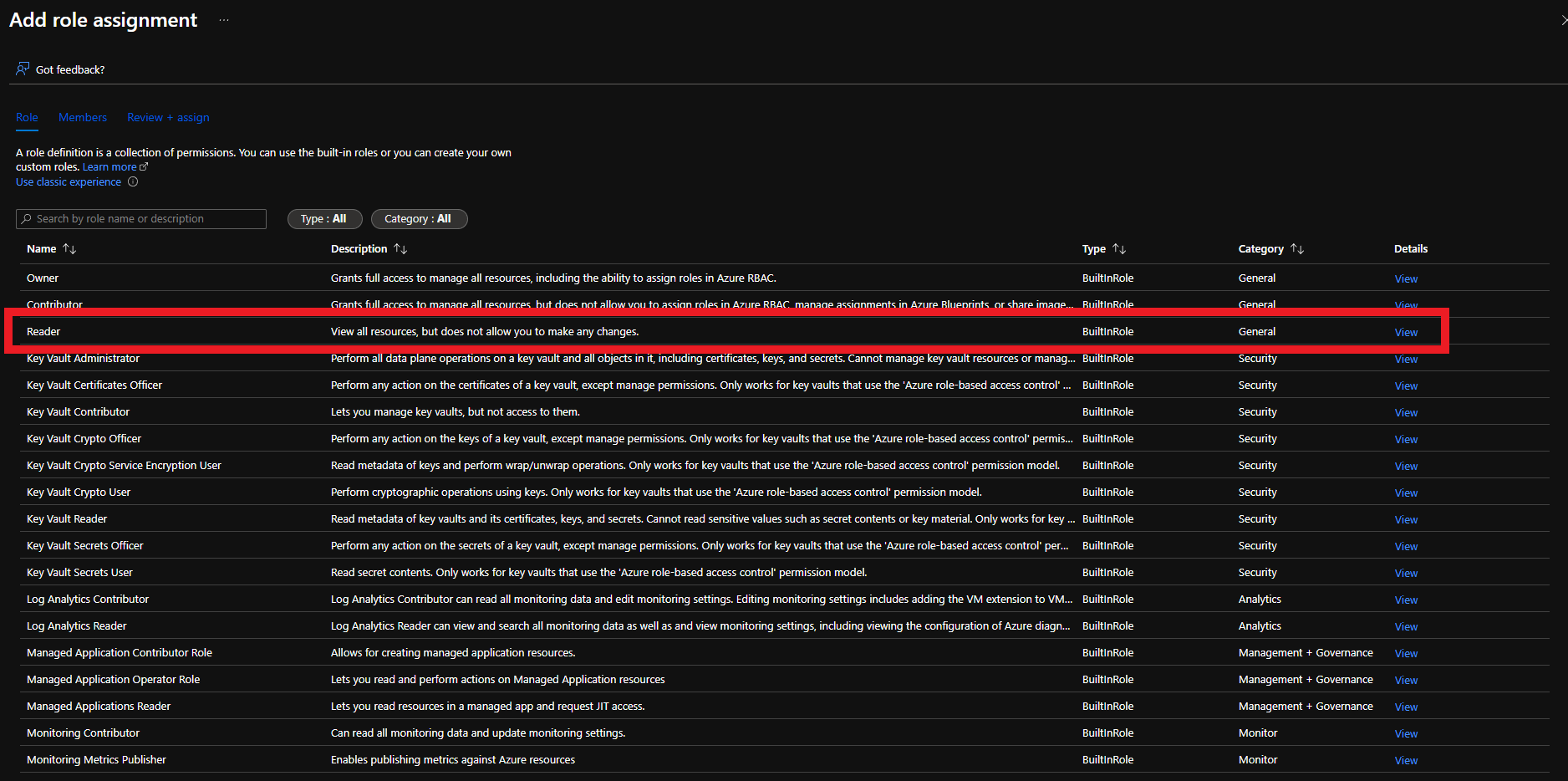
- Click on Members
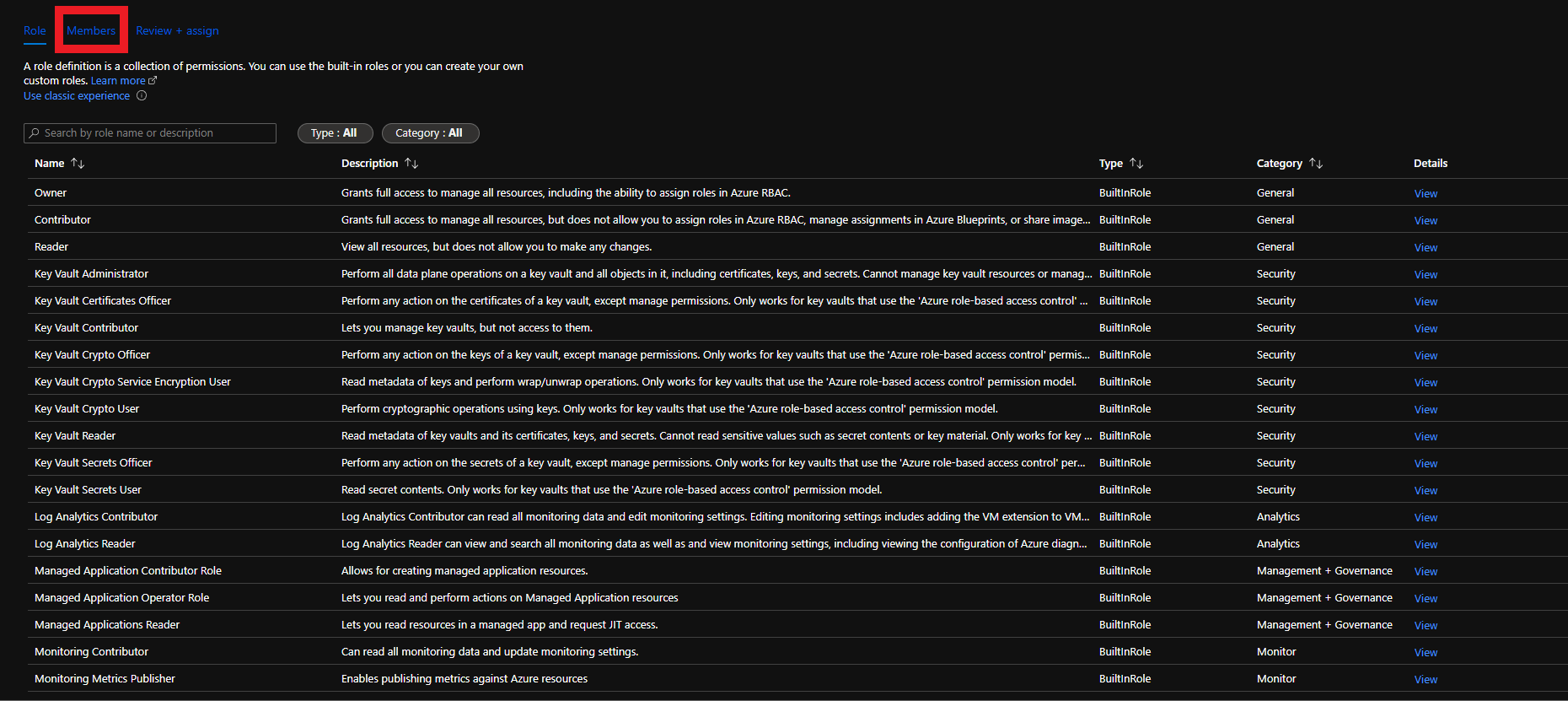
- Click on “Select Members”
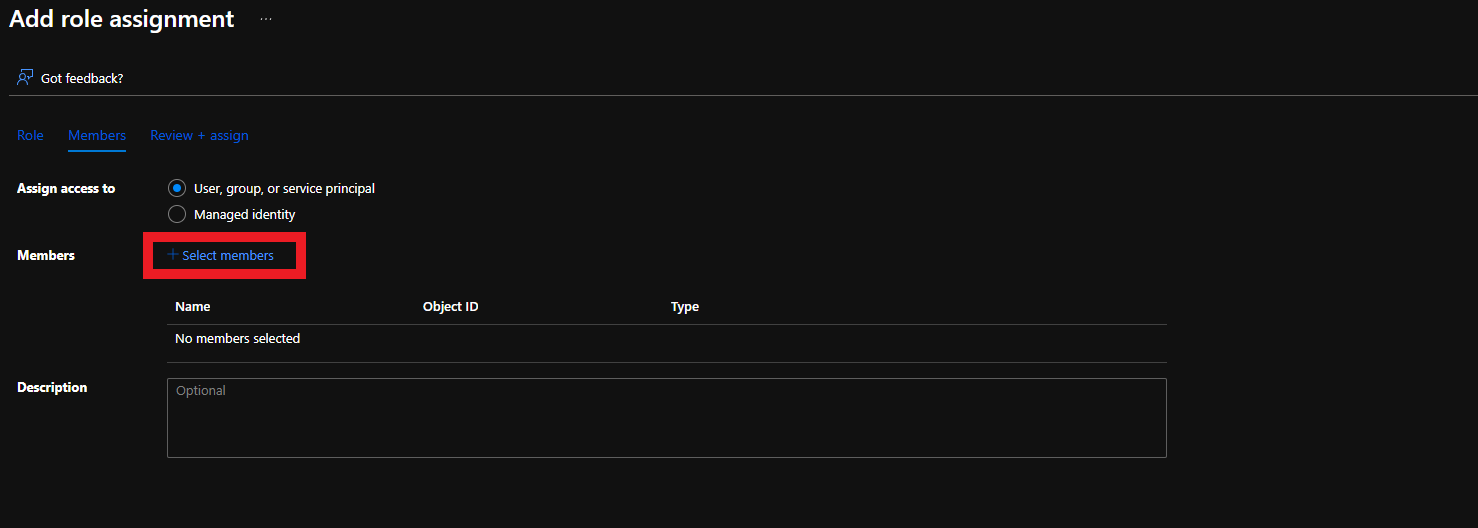
- Select the Keytos Application
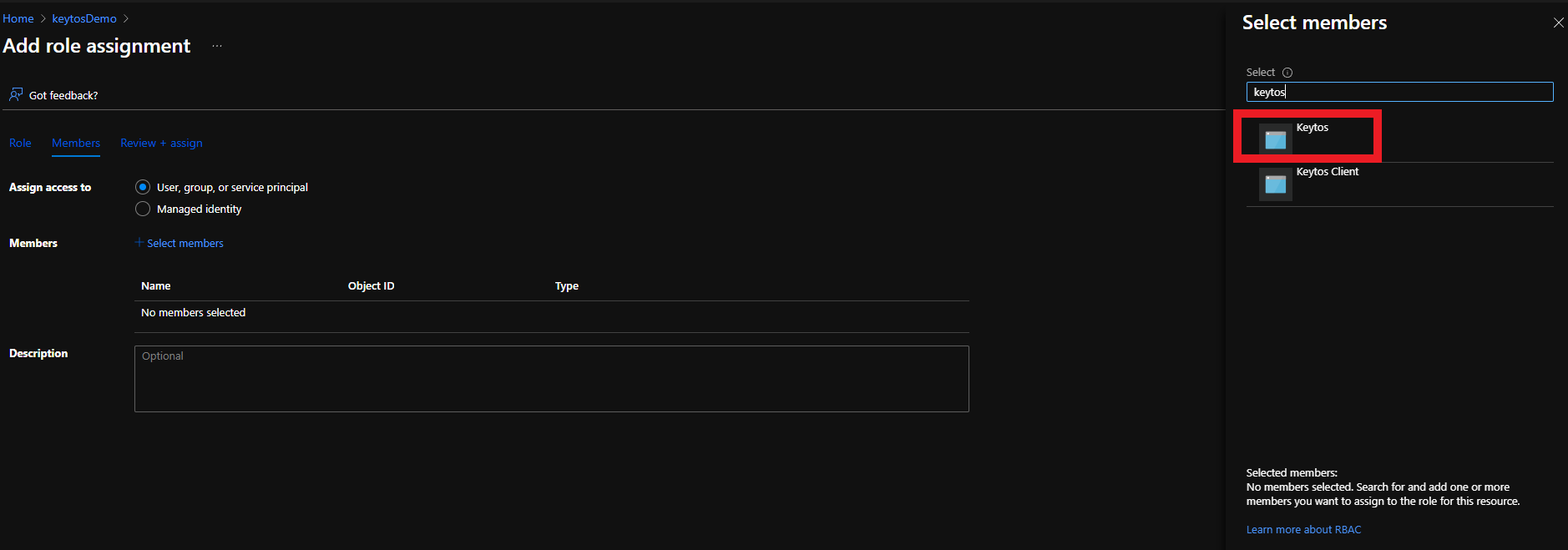
- Click the Select button
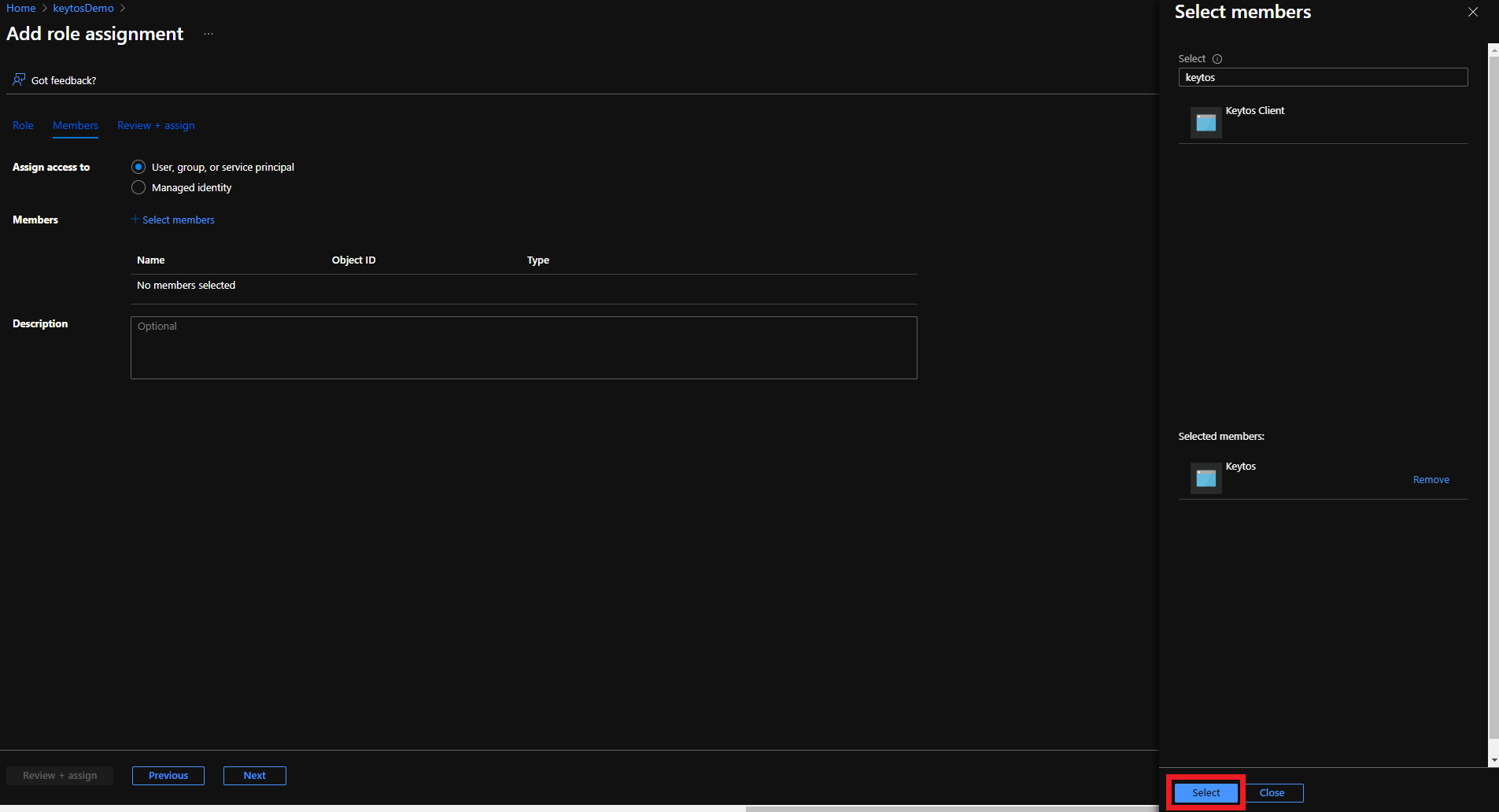
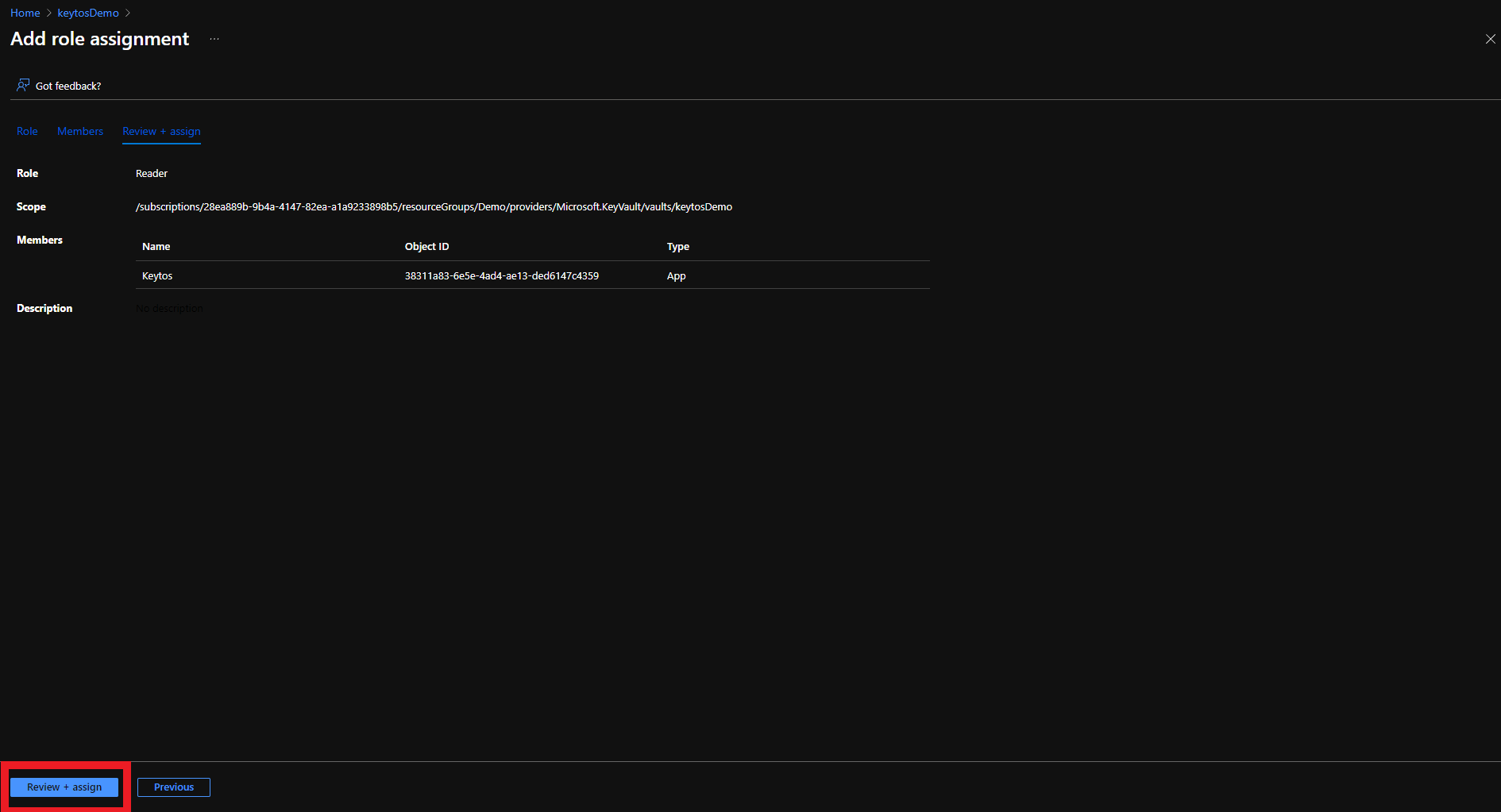
- Click the Review + assign button
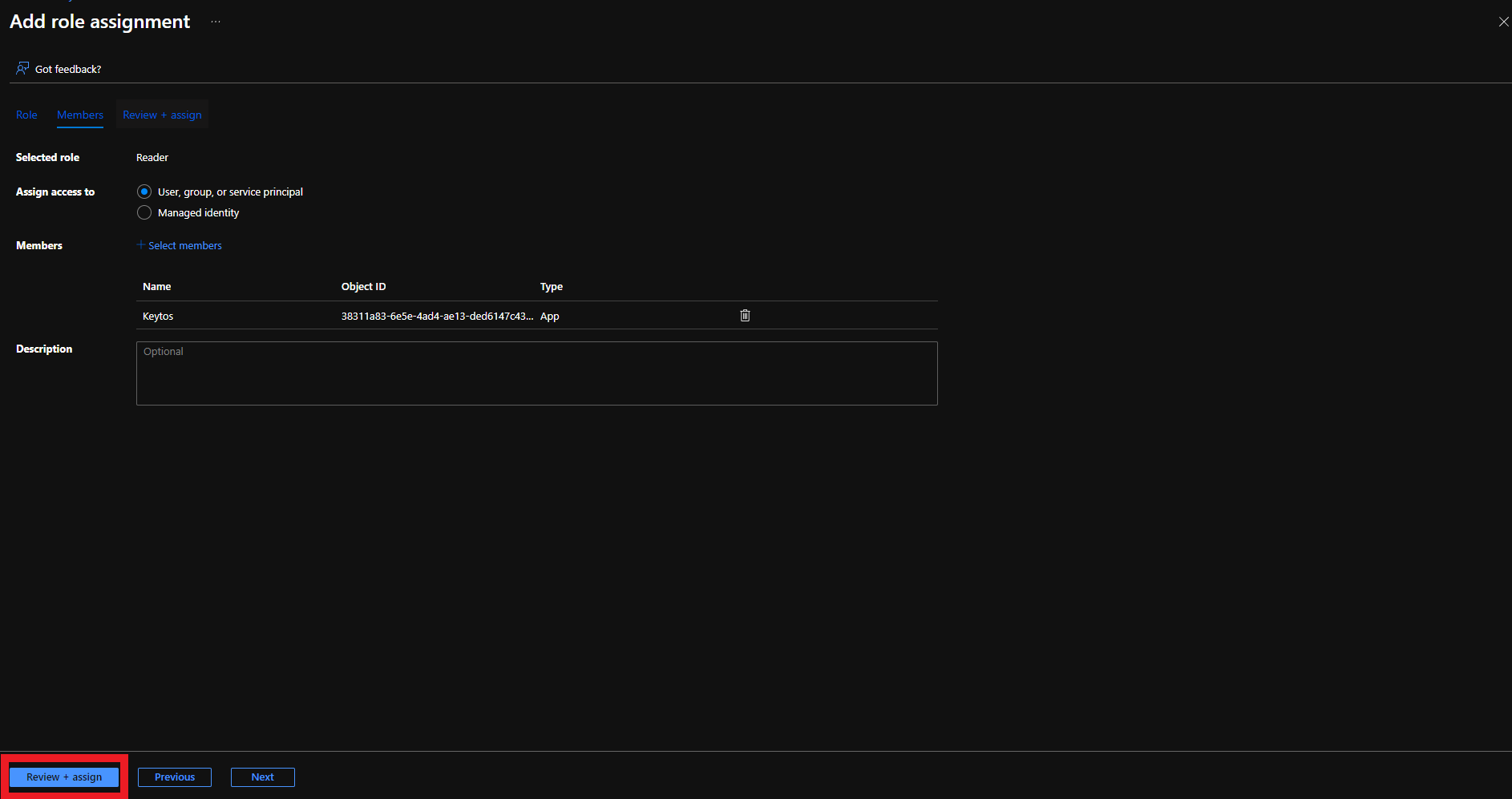
- Click the Review + assign button
Adding Application to Access Policies in Azure Portal
- Login to https://portal.azure.com
- Navigate to the Key Vault you want EZCA to manage.
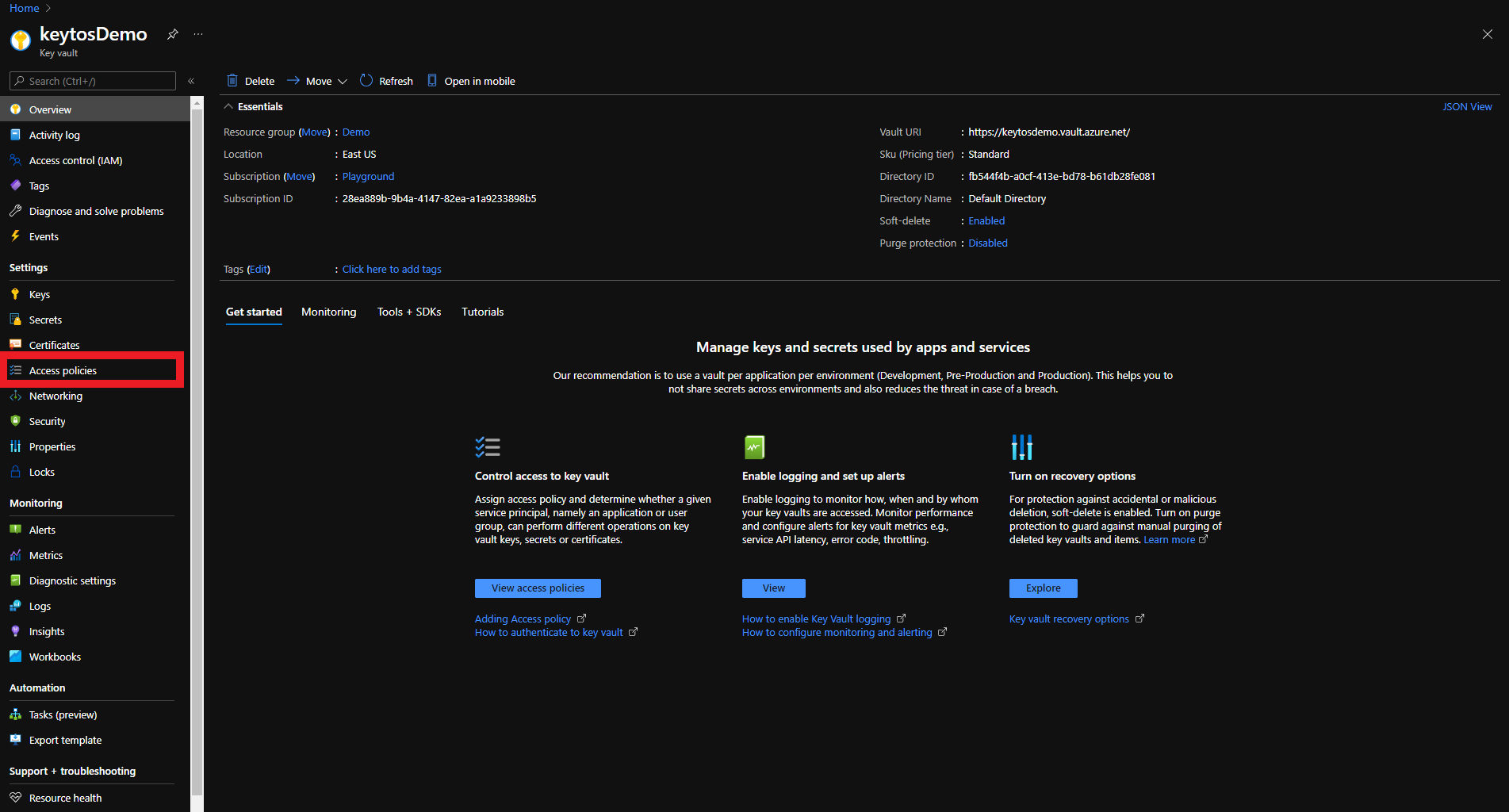
- Click on the Access policies menu option
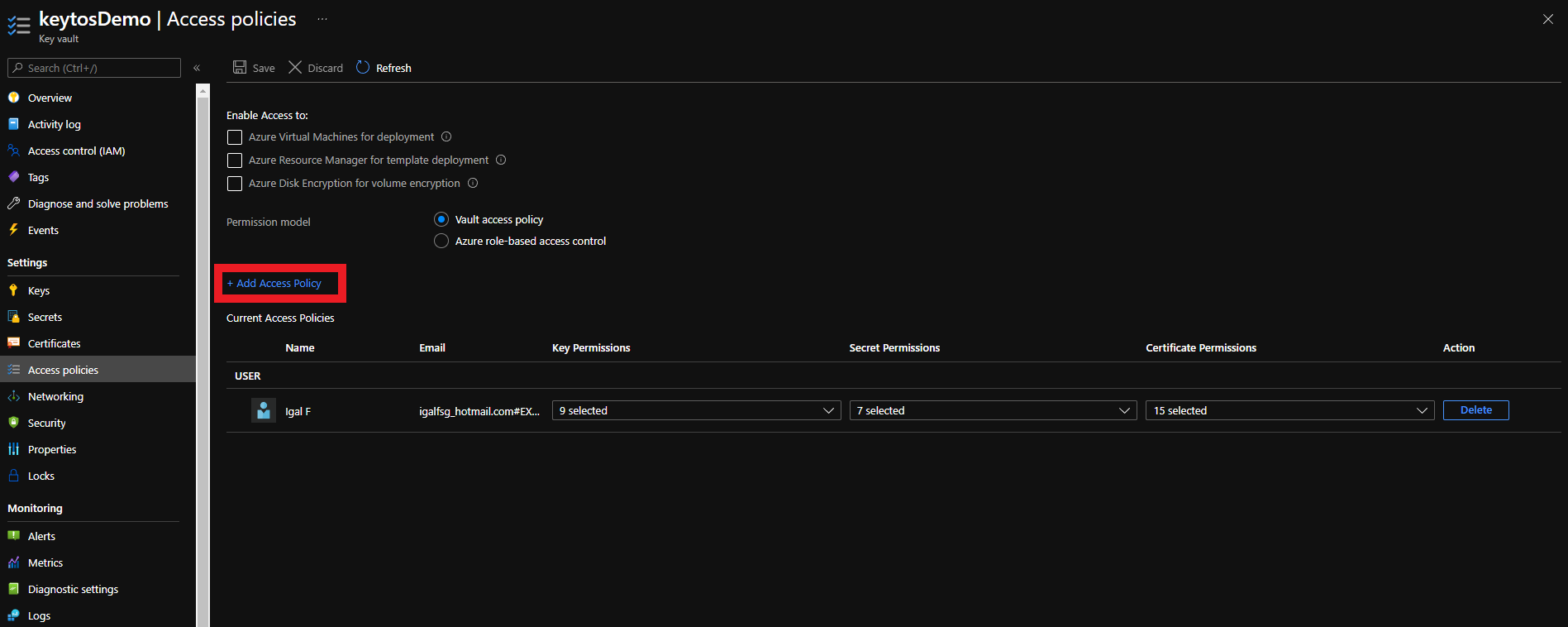
- Click on Add Access Policy
- Under Certificate permissions select: Get, Update, Create.
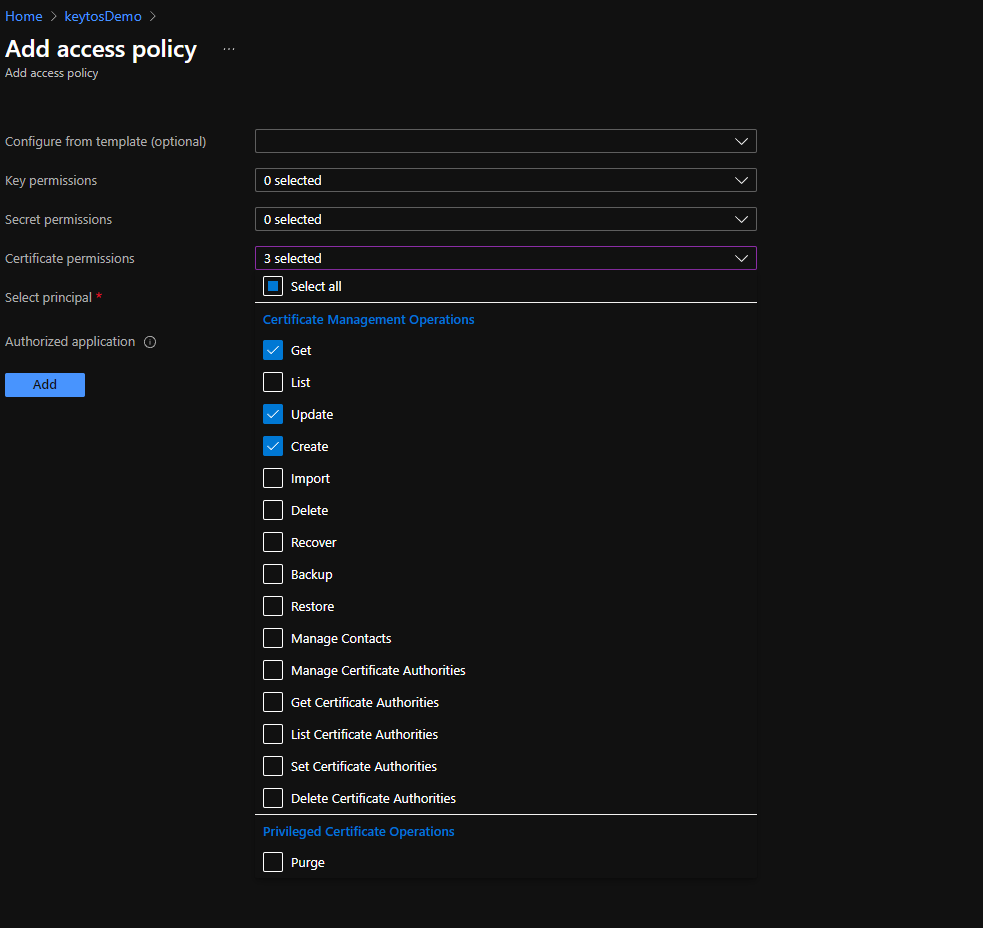
- Click on the “None selected” link to the right of Select Principal
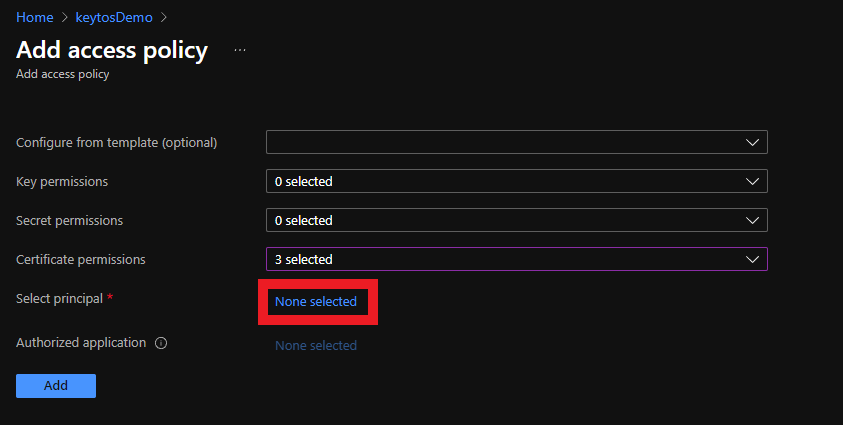
- Click on the “None selected” link to the right of Select Principal

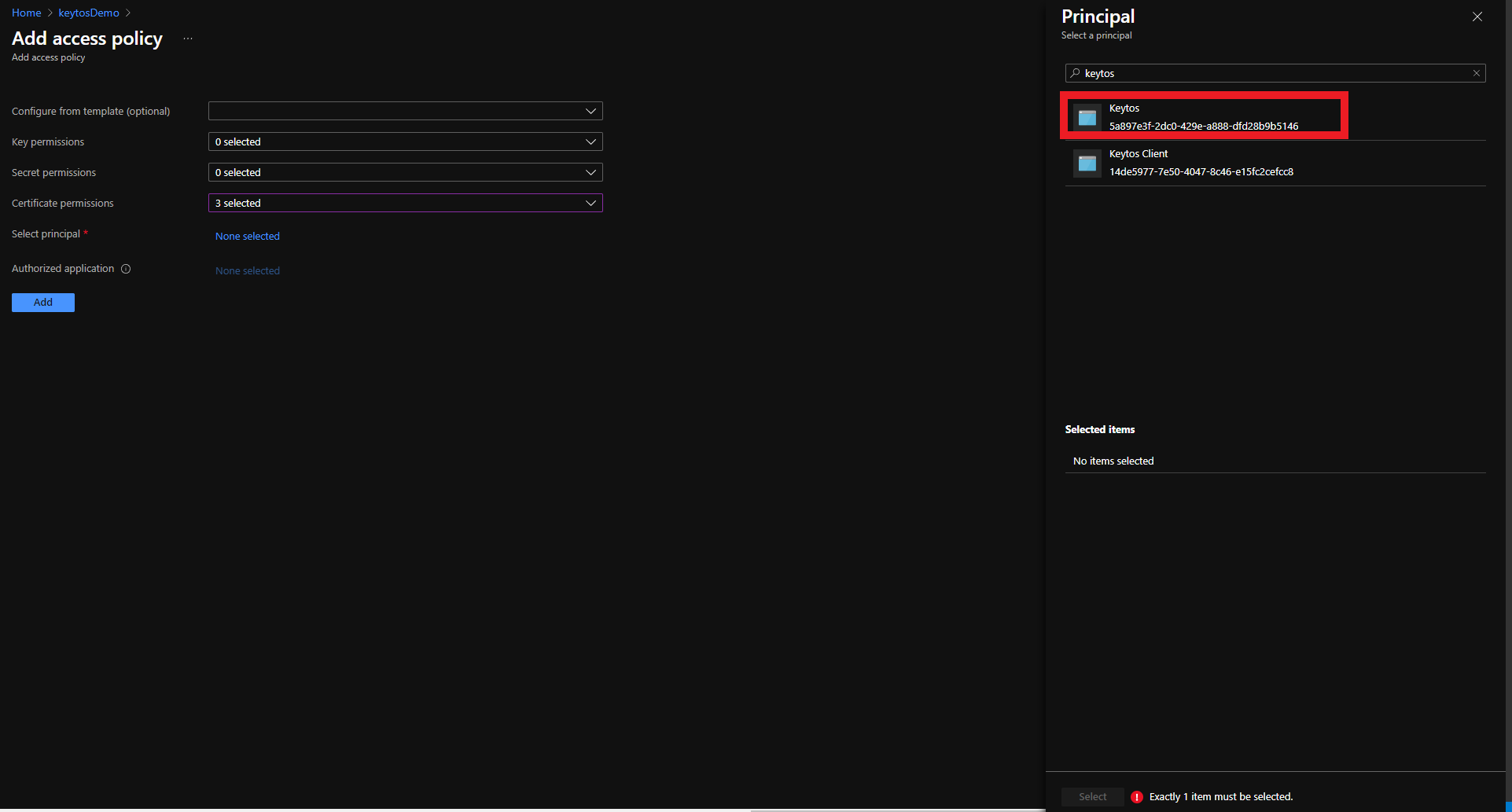
- Select the Keytos Application
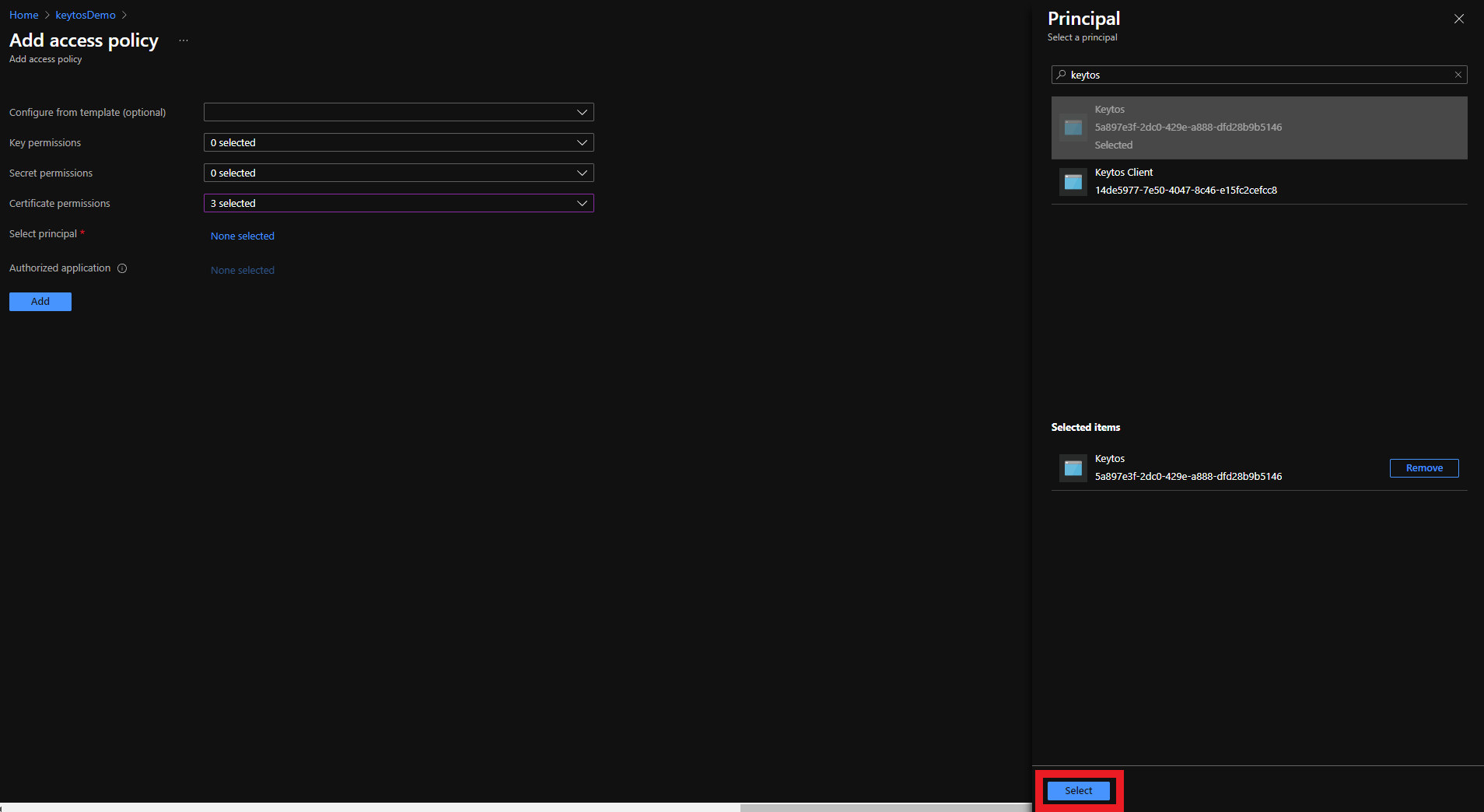
- Click the Select button
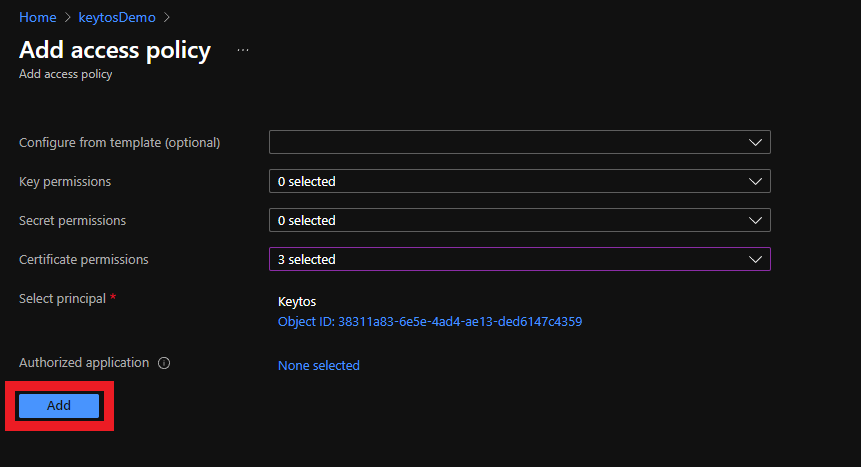
- Click the Add button
- Click the Save button
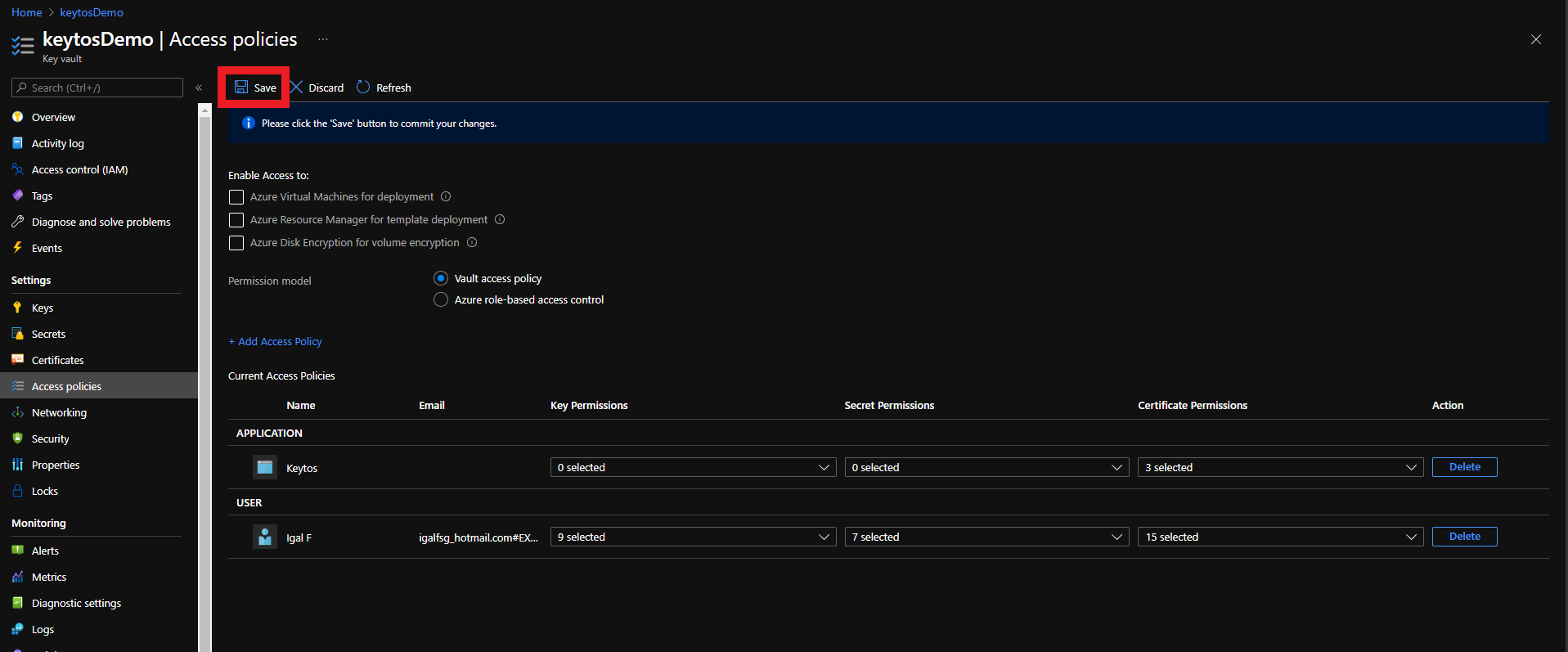
- Your Azure Key Vault is ready to be managed by EZCA!